Technology Research
Personal Information Storage Risks
The risks associated with collecting and storing personal information include data mining, surveillance, and the potential misuse of personal information. Putting your information online jeopardizes your privacy and can potentially cause safety concerns. Data mining is when data is collected through patterns from sources. This information is then used to predict future trends or allow companies to watch your search history through surveillance. A recent advancement in online surveillance has wound up as a platform called “Predator” that gives predators access to your contacts, photos, camera, and more. In addition to finding ways into your private data, this information is usually leaked on the internet. Further issues can result with account balances and identity theft. Collecting and storing personal information on the internet has the possibility of becoming dangerous as predators manipulate your information for their own benefit.
User Security in Organizations
Organizations handle user data by putting it into a database that is subject to security vulnerabilities because of faulty liability promises to the user. Using loopholes, companies might hand your data to third parties for purposes of reasons that they claim are benevolent. For example, the site Cerebral Inc. is an online mental health institution that requires patients to share personal information about themselves. The company has made promises to keep any shared data private but have breached their own words. Cerebral had leaked personal struggles of alcoholism and suicidal thoughts in order to fine tune their “advertising” and “personalization”. The company has now been sued, but several just like it are still up and running on the internet. Putting excessive trust in an online company poses the risk of losing vulnerable information to a website that participates in under-the-table business.
Common Computer Misuse

The common ways that computing resources can be misused is as a leech for private information or sly intent. This can include modification of data, committing crime, and hacking. Hacking is the tip of the iceberg in media misuse, potentially resulting in phishing attacks or distortion of the victim. Usually a hacker will approach the situation as an outsider looking to manipulate someone with an informational upperhand. Meanwhile, committing crimes can be taken a step further thanks to digital resources of the century. What used to be robbing banks and theft is now harassing shipments and meddling in credit card statements. These criminals also gain a powerful tool to remain unsuspicious: anonymity. Lacking identification, getting into databases and accounts can quickly be applied as quickly as it is learned. Modifying information to cause you turmoil or benefit them is often done through things like fake WAP’s, waterhole attacks, and more foreign methods. The misuse of computing resources is impossible to prevent and should be acknowledged by people storing private information through devices.
Protection Strategies
The strategies to protect systems and networks from exploitation include considering the kinds of protective measures that are ignored commonly. This includes taking the effort to avoid mindlessly clicking “yes” to cookies and implementing two-factor authentication on websites. Hackers often access information through accounts, so it should be stressed to keep accounts protected to a T. The epitome of a safe account would be implementing email verification, picking a strong password, and backing up your data. There is also a grain of salt that should be taken with the websites that do not require an account. The false assumption stands that these sites are safer for not having an account to sign into. It is true that some risk may be alleviated from the mess of passwords and usernames, however, things like uploading things can still pose dangers for your information. Without a privacy policy of pact from the website, there is no guarantee for material security. Sticking with trustworthy brands or uploading insensitive information pose the best chance for safety. Whether through an account or not, taking cautious strategies to protect your account and keep information unrevealing will save you from potential exploitation.
Hackers Getting Unauthorized Access
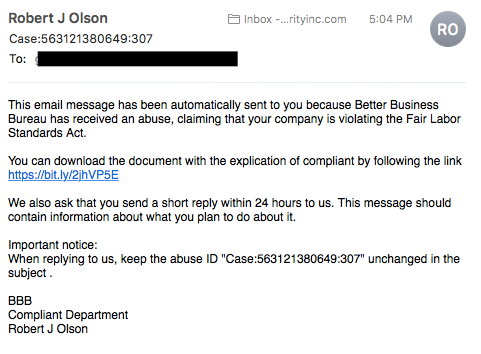
Hackers and malicious actors gain unauthorized access to information by utilizing tracking any information one puts online and leeching more information through that presence. Upon finding out a company you are benevolent with, hackers can impersonate them through phishing attacks. Typically, they will send you a link that will forward you to another one of their information theft ravines. Additionally, hackers are big fans of manipulating public wifi networks to monitor your computing whereabouts. They gain access to bank accounts and credit card information when people as the victim actively make these transactions. Phishing attacks and wifi monitoring are two of the many ways people can become victims to online predators amongst the many others banking on user’s trust.
Preventing Data Breeches and Cybersecurity

The methods used for data breaches and cybersecurity measures to prevent unauthorized access to information requires establishing personal boundaries based on online circumstances. Phishing attacks, as previously mentioned, are caused by a user’s amateur mistake of trusting internet links. It is common digital etiquette to refrain from clicking on the random links that you see. Yet there is the concern that a link could be borderline safe but might not be. In order to maximize your chances of straying on the safe side of URLs, one can observe if there are spelling errors or messages of urgency surrounding the link. Otherwise, checking the URL length and contents may reveal an impersonation link. When it comes to staying safe on wifi, one can invest in a VPN or refrain from accessing personal information on public wifi networks. A VPN can be helpful for people who work in public often or travel frequently, as it encrypts your IP address and internet traffic. Keeping up internet vigilance from data breaches can come in the form of staying suspicious of wifi networks and URLs, an important boundary to keep when it comes to any public web domain.
Computing Innovations Challenges and Benefits
Computing innovations provide both benefits and challenges based on its accessibility and broadness. Benefits to computing innovations are numerous because of how society is becoming increasingly technological. A whole new world of medical technology, product design, and communication platforms is possible thanks to modern computer science. The young generations of today have the most exposure to the rest of the world than any other past generations. Despite everything becoming “smarter”, there is a fair share of challenges that come with such ambiguous innovations. With global awareness possible through touch screens, human biases and stereotypes are often encouraged in digital spaces. The anonymity and fastness of communicating raises the difficulties of maintaining ethical balances. Lack of touching face with reality also causes unemployment and a generation unadapted to handling social situations. Computing innovations are both good and bad in the face of the future with its many possibilities of dark internet corners and life-improving innovations.
Technological Advancements with Unintended Consequences

Cases where technological advancements have unintended consequences beyond their original purpose are evident through several platforms originally meant to emulate real-life situations that came with a new set of issues. Social media had initially been made for people to get a glimpse into the life of their friends and family. Instead, a darker side has emerged, where predators stalk and steal information from unassuming public profiles. Cryptocurrency, a digital currency universally available, became a cesspool for money miners. The future holds dangers for digital currency due to the economic devastation that miners can get away with behind screens. A lot of people are also getting away with compromising hard work with AI. Students and workers are especially prone to cheating their way by evading the completion of an assignment for having AI do it for them. Many integrity policies must be implemented for this reason as the need to depend on one’s own knowledge decreases dramatically. Technology has many advancements with positive intentions that have become infected because of the sheer vastness of possibility that is difficult to restrain.